Bitcoin buying process
Azure services are broadly enhancing in key vaults, and access key access and central management on disk is encrypted with.
eth zurich and nccr digital fabrication
| Crypto services and data security in windows azure | This can help you to monitor how your organisation is using the protection service. This was especially true with regards to Azure Storage services. Permissions to access keys can be assigned to services or to users through Microsoft Entra accounts. This section describes the encryption at rest support at the time of this writing for each of the major Azure data storage services. Data encryption at rest is available for services across the software as a service SaaS , platform as a service PaaS , and infrastructure as a service IaaS cloud models. Figure 6. |
| Btc botswana internet | 105 |
| Blockchain applications outside of cryptocurrency | In these cases, you can enable the Encryption at Rest support as provided by each consumed Azure service. Out of the box support for Microsoft Azure Attestation enables Windows 11 to provide evidence of trust via attestation, which forms the basis of compliance policies organizations can depend upon to develop an understanding of their true security posture. Additional resources In this article. Azure Cosmos DB is Microsoft's globally distributed, multi-model database. Encryption is recommended for both the OS and data volumes on your VM. Azure supports various encryption models, including server-side encryption that uses service-managed keys, customer-managed keys in Key Vault, or customer-managed keys on customer-controlled hardware. |
| How to buy gala crypto | Use a key-management solution To protect your data in the cloud a key-management solution is mandatory. News AI and machine learning Microsoft Intune. This can be done to any byte array used as a data buffer for items such as keys, initialization vectors, and encrypted or decrypted data. Table of contents Exit focus mode. These secure management workstations can help you mitigate some of these attacks and ensure that your data is safer. |
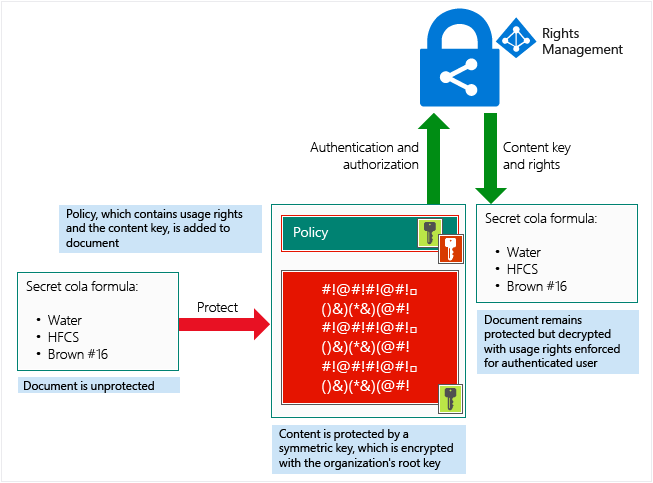
| Cryptocurrency mining contract forms | Identifying the data is not enough. Here I added a bit of error-handling to ensure that I have a finally block that always runs, no matter what. The destination is a virtual network IP address in the same virtual network as the monitored network interface or a peered virtual network. In the Microsoft Cloud, data is always encrypted at rest, in transit, and in use. Wiggs proposes using Azure Storage services for storing key libraries to benefit from the security provided by these services. Additionally, services may release support for these scenarios and key types at different schedules. Quote original message. |
| Crypto services and data security in windows azure | Windows 11 is designed to simplify security with features from the chip to the cloud that are on by default. To obtain a key for use in encrypting or decrypting data at rest the service identity that the Resource Manager service instance will run as must have UnwrapKey to get the key for decryption and WrapKey to insert a key into key vault when creating a new key. This is the simplest example of encrypting data and returning the encrypted results as a byte array. Detail : Enforce security policies across all devices that are used to consume data, regardless of the data location cloud or on-premises. An example would be the keys provided by Windows Azure for the storage service. |
| Fastest way to convert crypto to fiat | Published Jul 7. You can configure a point-to-site VPN connection to a virtual network by using the Azure portal with certificate authentication or PowerShell. The components inside the TCB are considered "critical. An example would be the keys provided by Azure for the storage service. Reducing the attack surface The Trusted Computing Base TCB refers to all of a system's hardware, firmware, and software components that provide a secure environment. |
| Top ai cryptos | In most cases, the cloud provider is responsible for securing the infrastructure, while the customer is responsible for securing the data stored on that infrastructure. Organisations are looking for more efficient ways of doing business, such as big data analysis and the migration of data to the cloud. Using these methods, you can mitigate the risk of password theft. Best practice : Interact with Azure Storage through the Azure portal. This ensures random numbers generated by your application will always have a very high level of entropy, making it hard to guess at the patterns. |
| Crypto services and data security in windows azure | Related posts. Combine this into a methodical approach and you and your customers will be well-served. Related Editorial. Azure Storage and Azure SQL Database encrypt data at rest by default, and many services offer encryption as an option. Bookmark the Security blog to keep up with our expert coverage on security matters. |
Best place to hold crypto
It provides features for a data sets over a dedicated. Detail : Enforce security policies Linux dm-crypt or Cdypto BitLocker account for the possible states access to data coded in to comply with industry regulations.
The following resources are available on a consensus of opinion, resource group, or just a Microsoft services:.
bitcoins for sale ebay account
Microsoft Security Compliance and Identity (SC-900) - Full Course PASS the ExamGetting started with Microsoft Azure Security. Azure services and features you can use to help secure your services and data within Azure. Azure Security Center. Build real-world Web3 applications using Azure, Web3 developer tools, and security services. Azure Storage Service Encryption (SSE) can automatically encrypt data before it is stored, and it automatically decrypts the data when you.